Open Source Software Security
OPEN SOURCE SOFTWARE SEARCH
Protect your software supply chain by identifying contributors with ties to state-sponsored entities in your open source code.
The Intelligence Powering the Most Advanced OSS Threat Detection
Strider’s proprietary data engine ingests billions of global documents to power precise insights into open-source contributors and dependencies.
10B+
Documents in Database
92K
Global Data Sources
12M+
New Documents Added Daily

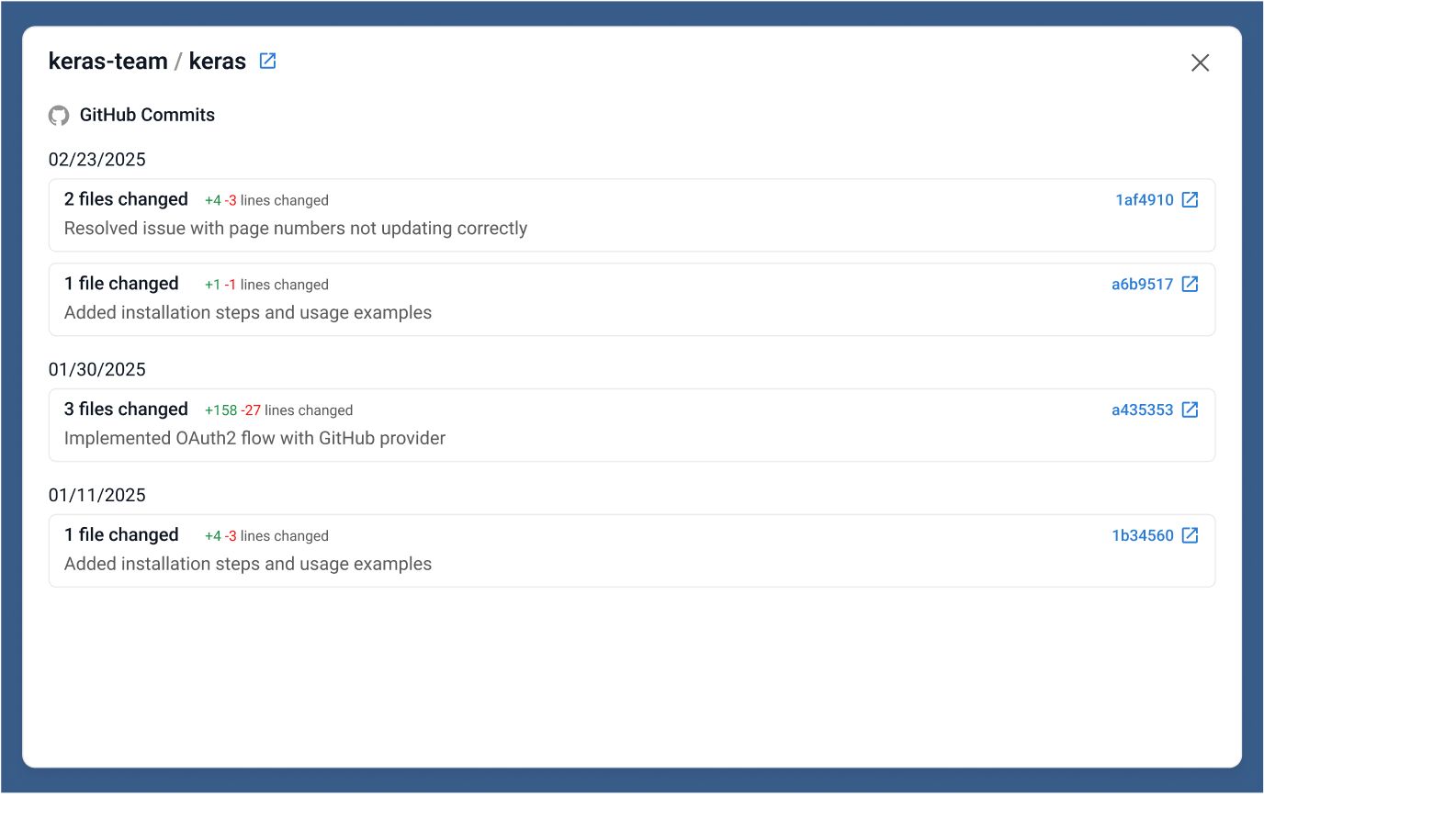
Open Source Threat Monitoring
Continuous OSS Surveillance
Strider delivers ongoing scans of your open source dependencies and contributor activity so you can detect emerging threats early and maintain security throughout the software development lifecycle.
Proactive Threat Detection: Identify nation-state risks and vulnerabilities before they impact your codebase.
Always-Up-to-Date Visibility: Receive continuous intelligence that reflects the latest changes in your open source ecosystem.
Reduce Operational Load: Automate OSS monitoring and free your team from manual, incomplete reviews.
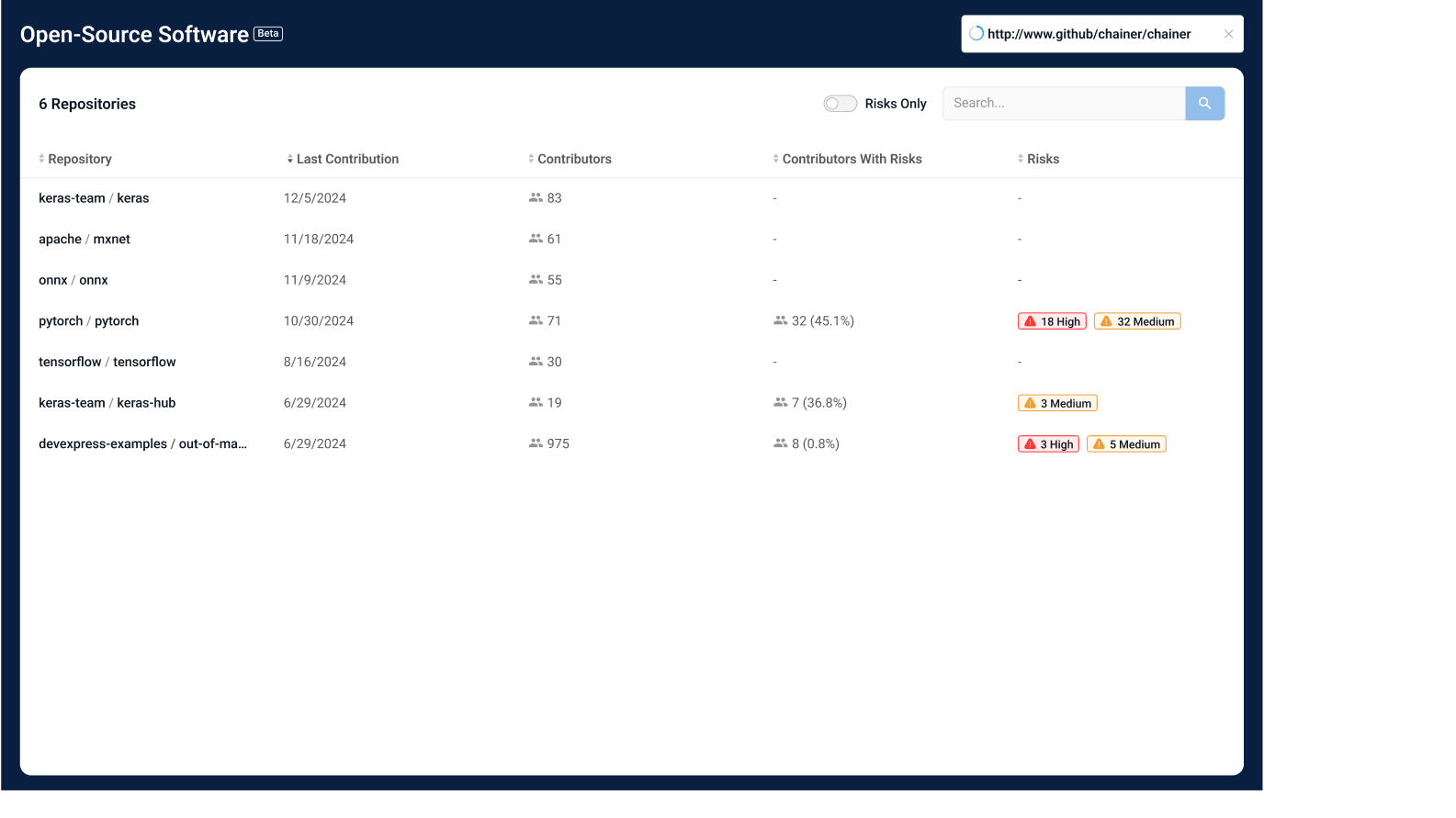
Open Source Vulnerability Management
Illuminate Hidden Threats in Your OSS Stack
Strider maps your open source dependencies—including nested and transitive layers—to expose hidden risks. Advanced analytics surface indirect ties to state-sponsored actors, giving you full-spectrum visibility across your OSS environment.
Expose Deep Vulnerabilities: Uncover risks buried in nested and transitive dependencies—not just surface-level code.
Focus on What Matters: Get prioritized, actionable insights so your team can target the most critical threats first.
Improve Strategic Defense: See the full picture of your OSS exposure and allocate resources where they’ll have the most impact.
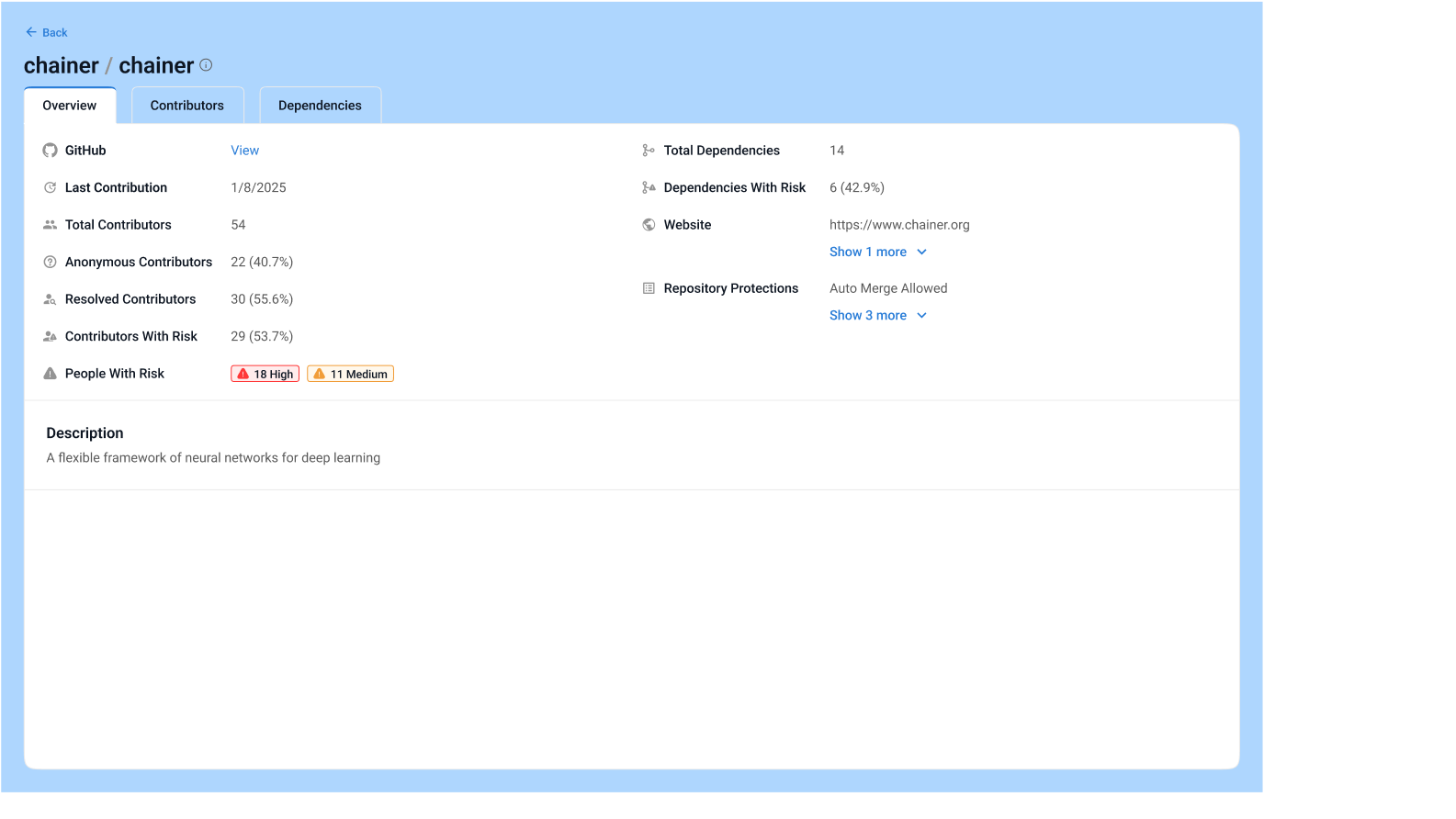
Open Source Contributor Risk Assessment
Know Who’s Behind Your Code
Strider reveals who’s behind the open source libraries in your stack—mapping affiliations, commit activity, and risk signals to identify potential insider threats and state-sponsored links before they cause harm.
Understand Contributor Impact: See not just who’s contributing, but what they’re contributing and how it affects your codebase
Surface Hidden Affiliations: Detect ties to suspicious organizations or foreign actors using proprietary risk modeling and historical analysis.
Strengthen Code Integrity: Mitigate threats from high-risk contributors and ensure safer, more secure OSS adoption.
Use Cases
Real-World Applications
Strider OSS Search integrates seamlessly into critical security workflows, empowering teams to evaluate new packages, monitor existing dependencies, and assess third-party OSS risk during audits or M&A due diligence. With targeted intelligence and continuous visibility, teams can make faster, more informed decisions across the development lifecycle.
Vetting New Open Source Libraries
Assess contributor risk and software integrity before developers bring new open-source packages into your environment.
Ongoing Monitoring of OSS Dependencies
Track contributor changes, threat signals, and risk shifts across actively used libraries—automatically and continuously.
Supply Chain Risk Assessments for M&A and Vendor Audits
Evaluate the OSS posture of third-party software to inform acquisition decisions, vendor onboarding, and compliance reviews.